Optimized and secured computer systems are vital to keep your business moving. When it comes to IT and cybersecurity, we’re dedicated to providing the best to our clients. Discover how we can position your company for profitability and success. Read More
RIGHT FIT MEETING


ASSESSMENT
DISCOVERY & ONBOARDING


IMPLEMENTATION
SERVICE DELIVERY & QUARTERLY BUSINESS REVIEWS

Swift Chip provides managed IT and cybersecurity services for a wide variety of companies in fields with stringent privacy and compliance requirements. Read More
FINANCIAL SERVICES
LEGAL
MANUFACTURING
MEDICAL
NON PROFIT
TECHNOLOGY
Ransomware threats, cyberattacks, and data breaches can cripple your business. Understand your options for preventing major losses and lawsuits.
From eMail security to network challenges in the office, save time and hassle when you outsource your IT support with our team of dedicated IT professionals.
Moving your business forward means having IT infrastructure that can keep up with growing demands. For small- to medium-sized enterprises, sparing the time from the pressing day-to-day needs of running…
Read MoreAchieve workplace modernization on a budget with Swift Chip’s Cloud Services. Our future-oriented solutions allow your organization to be sustainable, efficient, and competitive with freedom to scale resources as your…
Read MoreGetting the most out of your technology means making sure that you and your staff are comfortable and proficient with your systems and software. Swift Chip can help existing employees…
Read More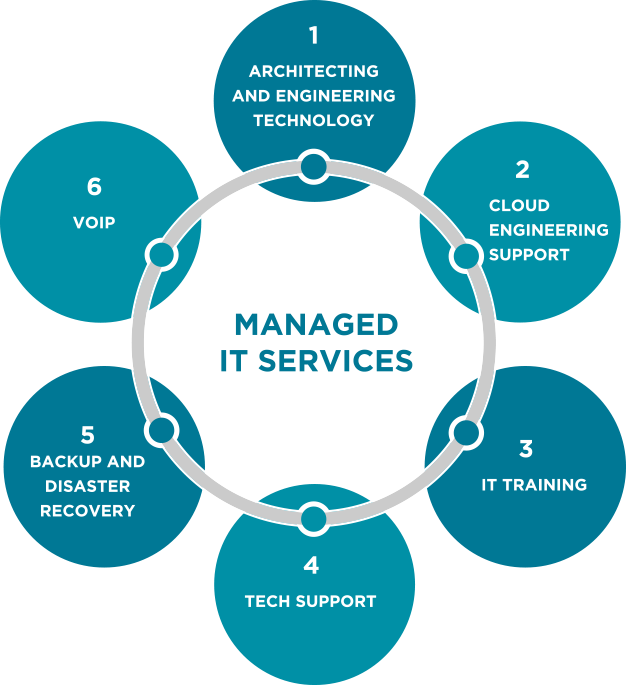
News, tips, and insights on issues related to IT, cybersecurity, emerging online threats, and more.
Did you know that cyber crime is predicted to cost the world $10.5 trillion annually by 2025? Don't let your business become a statistic! Utilize the knowledge and practical strategies presented in our Cyber Security Essentials booklet to navigate the ever-evolving digital landscape with greater confidence and peace of mind. Fortify your business against cyber threats—download your copy now and invest in a more secure future!
Uncover a unique fusion of ancient wisdom and modern cybersecurity in 'The Art of Hacking: Ancient Wisdom for Cybersecurity Defense' by Swift Chip's very own Certified Ethical Hacker, Ken May. Through thought-provoking questions like 'If Sun Tzu hacked you, how would you be able to stop him?' and 'What did the Samurai know about firewalls?', Ken reveals powerful insights and practical techniques for defending against today’s cyber threats. Equip yourself with a fresh, strategic approach to cybersecurity by downloading this one-of-a-kind book!
Swift Chip provides managed IT and cybersecurity services for a wide variety of companies in fields with stringent privacy and compliance requirements.